ExecutionPolicy Bypass vs Unrestricted in PowerShell
- PowerShell Execution Policies
- Customize the Execution Policy
-
PowerShell
BypassPolicy -
PowerShell
UnrestrictedPolicy
This article introduces the execution policies in PowerShell, Bypass and Unrestricted.
PowerShell Execution Policies
PowerShell is one of the most popular scripting languages among system administrators, security tests, and hackers. Windows is the most popular operating system for computers.
Therefore, millions of users are using it. Hence, PowerShell is used to automate workflows, call the Windows API, and write penetration test tools.
Due to many Windows users, Microsoft took measures to add some built-in security features. The execution policies are introduced to determine which type of PowerShell scripts can be executed on the system.
It doesn’t mean users are restricted from executing certain PowerShell scripts. Hence, the execution policies prevent unintentional script executions.
The Bypass and Unrestricted are two important execution policies. These two policies got very identical behaviors.
Customize the Execution Policy
PowerShell users can easily change the existing policy. The Set-ExecutionPolicy cmdlet is used to customize the PowerShell execution policies.
Syntax:
Set-ExecutionPolicy
[-ExecutionPolicy] <ExecutionPolicy>
[[-Scope] <ExecutionPolicyScope>]
[-Force]
[-WhatIf]
[-Confirm]
[<CommonParameters>]
The -ExecutionPolicy parameter specifies the PowerShell execution policy, such as Bypass and Unrestricted. Also, the -Scope flag can give the policy scope like Process, CurrentUser or LocalMachine.
PowerShell Bypass Policy
The Bypass policy is used to skip all Windows PowerShell security checks. The risk is Bypass policy allows you to run any PowerShell script without warnings or prompts.
Therefore, users need to be careful when using the Bypass policy. Usually, we use this policy for applications that include their security model.
The Bypass execution policy can be established as shown below.
Set-ExecutionPolicy -ExecutionPolicy Bypass
Output:
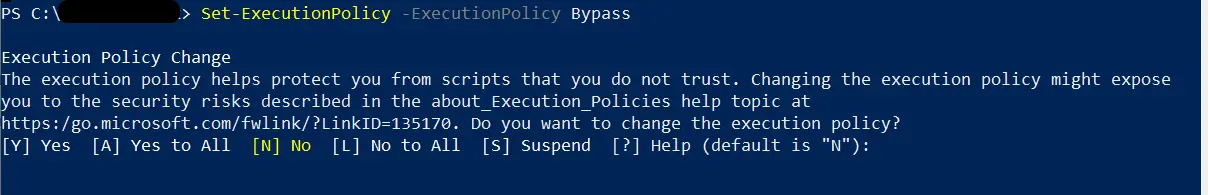
Since it allows you to execute any PowerShell script, PowerShell warns you because malicious scripts might run unintentionally and harm your private data. You need to run PowerShell with administrator privileges to change execution policies.
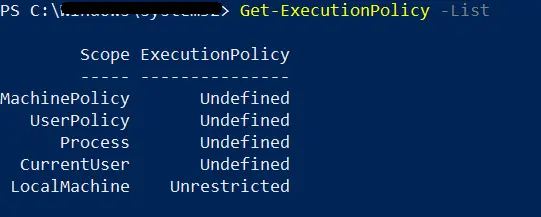
We can confirm the policy change using the Get-ExecutionPolicy cmdlet.
Get-ExecutionPolicy -List
Output:
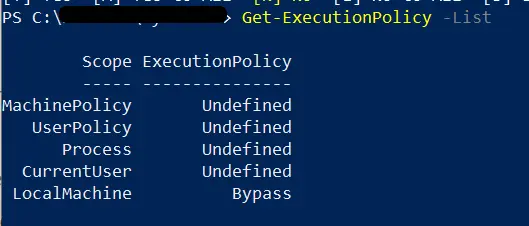
The policy change affected on LocalMachine scope.
PowerShell Unrestricted Policy
The Unrestricted policy is similar to the Bypass one. The major difference is that the Unrestricted policy will warn you and ask for the correct permissions before executing an unsigned script.
You can set this execution policy using the Set-ExecutionPolicy cmdlet.
Set-ExecutionPolicy -ExecutionPolicy Unrestricted
Output:
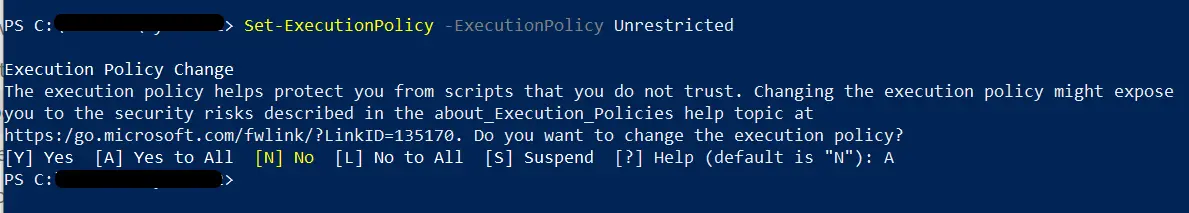
We can confirm the above change with the Get-ExecutionPolicy cmdlet.
Output:
Nimesha is a Full-stack Software Engineer for more than five years, he loves technology, as technology has the power to solve our many problems within just a minute. He have been contributing to various projects over the last 5+ years and working with almost all the so-called 03 tiers(DB, M-Tier, and Client). Recently, he has started working with DevOps technologies such as Azure administration, Kubernetes, Terraform automation, and Bash scripting as well.
